Why do we need anonymous internet access? In today's highly developed internet era, user privacy is just a talk.
No matter what industry we are in, we should protect our IP address to prevent malicious activities.

The application scenario here is that I am an internet worker, and while protecting myself on the internet, I also want to separate my normal life from the internet.
We can prepare some tools to work together to achieve the highest level of anonymity, such as VPN, jump server, Tor browser, residential IP, etc.
VPN#
This is the simplest and fastest anonymous method, whether it is a foreign VPN, an airport VPN, or a self-built VPN.
The threshold is very low, but it only provides one layer of proxy. The traceable path is VPN-local network.

If you just want to speed up your connection to your home country or watch videos, conduct academic research, etc., it is still very good.
Tor Browser#
Tor browser is very well-known for anonymity: https://www.torproject.org/zh-CN/
However, it is currently impossible to use it normally in the domestic network environment. Using a VPN to proxy Tor traffic will result in slower speed.
It is not impossible to use, but it is just a little slower.
So, the current traceable path for us is Tor bridge-VPN-local network.
Of course, this is just one method of use. We can also use a jump server to set up a network relay and control server to use Tor browser.
Jump Server#
For information on setting up a jump server, you can refer to my article Next Terminal: Lightweight and Easy-to-use Jump Server System, It's Really Elegant!
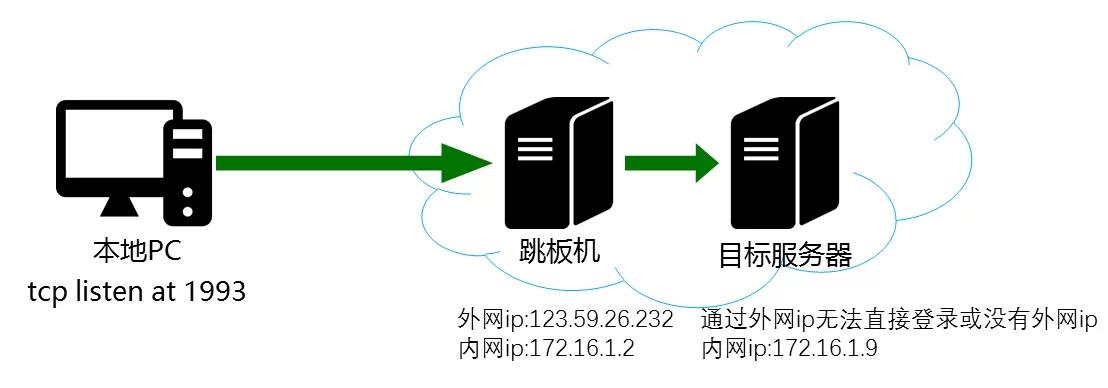
Of course, after setting up a jump server, you cannot use it with peace of mind. It is just a relay solution.
Currently, the commonly used solution is to use VPN to control the jump server, and the jump server connects to a remote Windows server to browse the internet.
Of course, the jump server can also be a Windows server directly.
The traceable path when using a jump server is: Windows server-jump server-VPN-local network.
Of course, we can also create a gateway in the jump server's system and use another server for link relay.
In this case, it would be: Windows server-intermediate server-jump server-VPN-local network.
Residential IP#
Currently, residential IPs are all overseas IPs and cannot be used within the Great Firewall. To achieve anonymity, residential IPs must be exposed at the outermost layer.
And the IP's country and province are all in the same city, making it more like you are abroad.
There are some limitations, and it can only be used in conjunction with a jump server.
Use local VPN to control the jump server, and the jump server connects to a remote server. The remote server uses the residential IP for internet traffic.
Compared to the previous method of using VPN to control the jump server and the jump server connecting to a remote Windows server to browse the internet, the advantage of exposing the residential IP at the outermost layer is significant, making it more like a real person.
Summary#
Among the four anonymous methods mentioned above, except for residential IP, the others can be used in combination.
I will provide several scenarios for setting up (ranked by anonymity level):
- VPN-Internet
- VPN-Windows jump server-Internet
- VPN-Tor browser-Internet
- VPN-Jump server-Windows server-Internet
- VPN-Jump server-Residential IP-Internet
- VPN-Jump server-Gateway relay-Windows server-Internet
- VPN-Jump server-Windows server-Residential IP-Internet
- VPN-Jump server-Gateway relay-Windows server-VPN-Internet
- VPN-Jump server-Gateway relay-Windows server-Tor browser-Internet
- VPN-Jump server-Gateway relay-Windows server-Residential IP-Internet