I came across a Trojan program in a Telegram group chat. It is simply a compressed package containing an exe software. The Trojan programs I have seen before were not so obvious. Most people would recognize these as Trojan files, but some may still be tempted to click on them or are simply unaware.
I also checked the profile of this person and found that they have a premium membership and their personal description states that the payment address has been changed. It seems like a friend who has had their account stolen by this program.
Trojan sample: Google Drive
Habo analysis: https://habo.qq.com/file/showdetail?pk=ADcGb11qB2cIOVs6U2I%3D
Kaspersky: https://opentip.kaspersky.com/C667BE786A5A67A74331E1FA7E2CEF2BC33B55739AD31B5456A3697623C6BACF/results?tab=upload
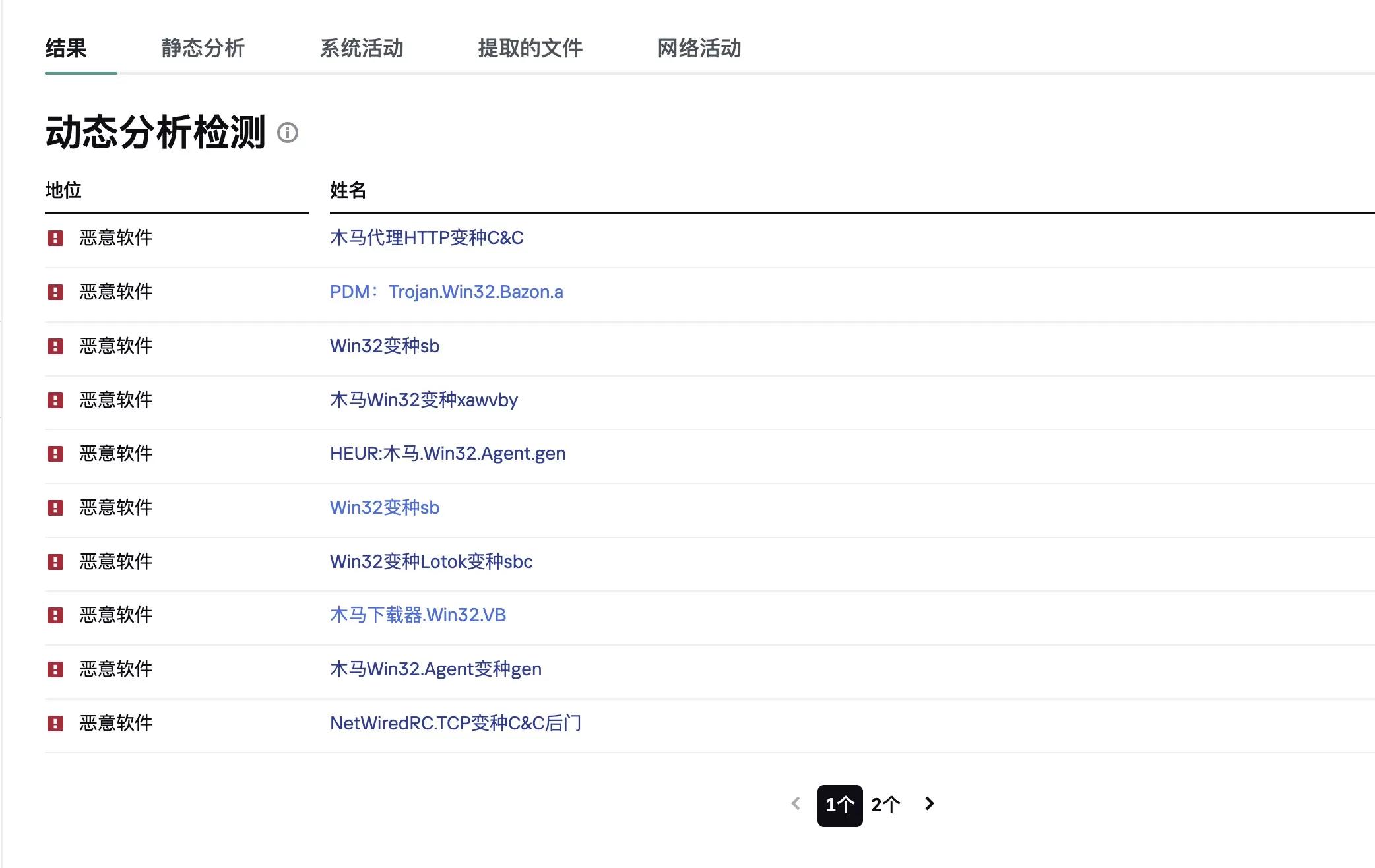
From the screenshot above, it is clear that this is a Trojan file without a doubt. Its main function is to monitor user activities electronically (intercepting keyboard input, capturing screenshots, capturing a list of active applications, etc.) and send the collected information to hackers through various means. It also employs various methods to prevent the program from being detected and gain complete control over the computer's files.
But I think any antivirus software should be able to detect this program. I scanned it with Huorong Security and found it to be dangerous!
Then I opened a virtual machine to capture the activity range of this software. I don't understand the technical details, so please don't laugh at me.
First, when I opened the software, nothing was displayed. After running in the background for a while, it closed. At this time, it sent requests to note.youdao.com:443 and bucket-ynote-online-cdn.note.youdao.com:443.
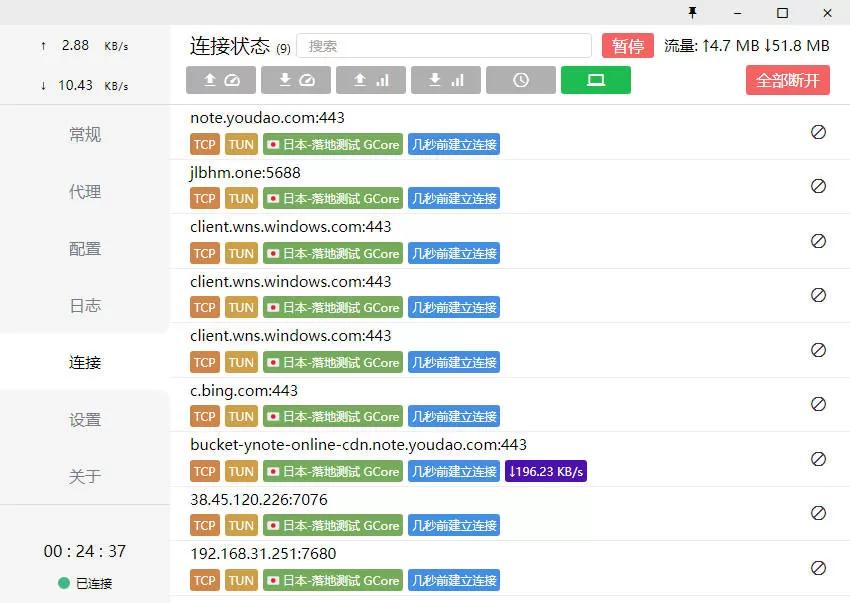
I used the tun mode of Clash for Windows and checked it in the Clash client. I wanted to protect my IP from being exposed, and using the virtual machine as a system proxy may not be followed.
Then a popup window appeared, and I don't know what it is for. It generated an exe file in the user directory.
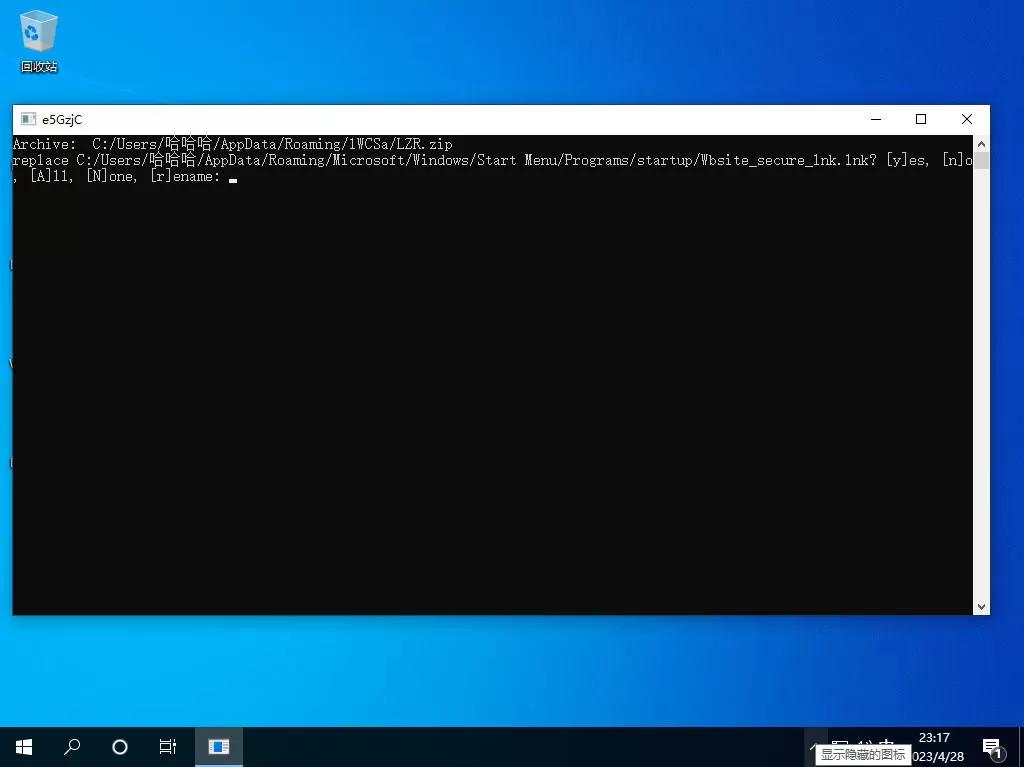
I uploaded the exe file to Kaspersky and didn't find any issues!
Then I noticed that it always sends requests to two addresses, 38.45.120.226:7076 and jlbhm.one:5688. I checked and found that this domain was recently registered.
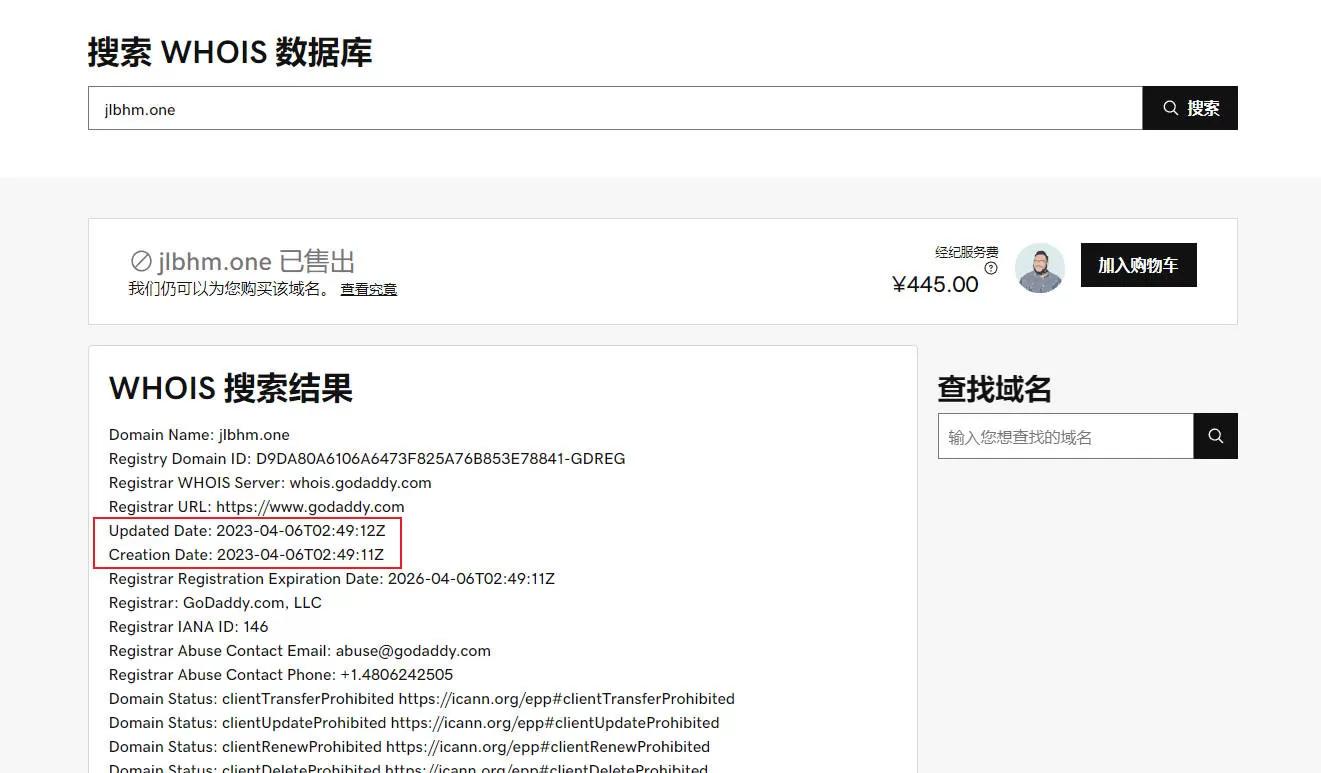
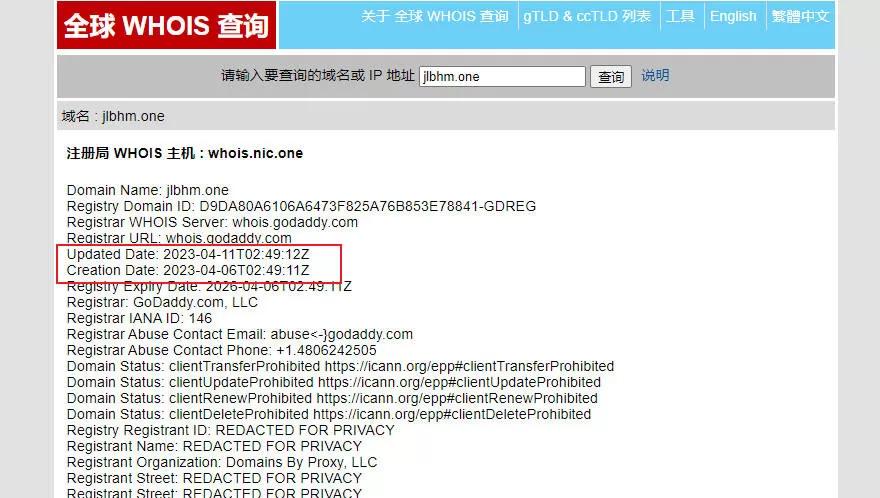
Furthermore, the jlbhm.one domain is not resolved, and 38.45.120.226:7076 is always in a connecting state, while jlbhm.one:5688 connects, disconnects, and then reconnects.
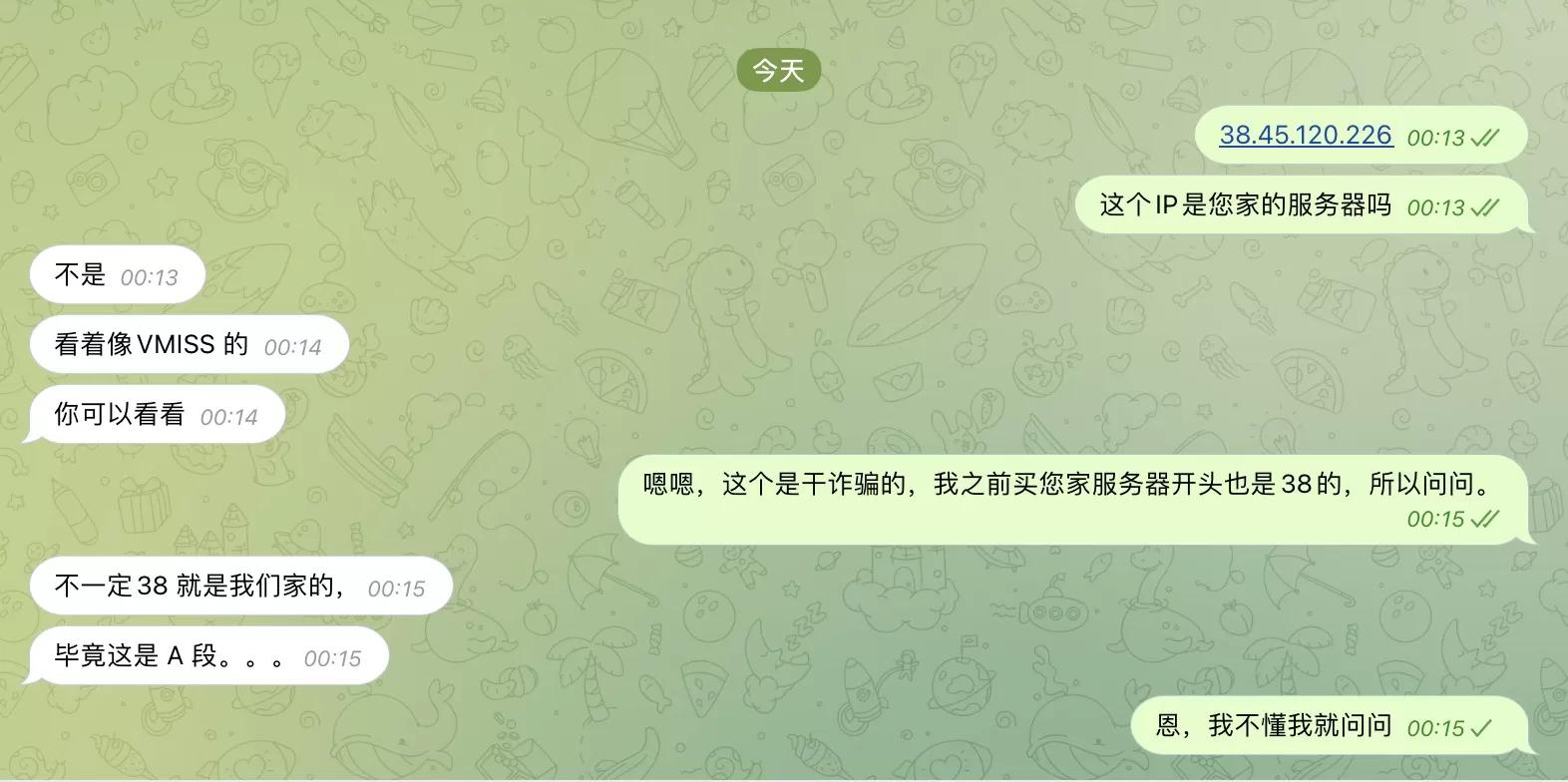
I used a webmaster tool to ping this IP: https://ping.chinaz.com/38.45.120.226. Can you guess what the result was?
The IP shows China Hong Kong Cogent, and I saw this IP starting with 38 and it felt familiar. After thinking for a while, I remembered that I saw someone recommend a Hong Kong CMI server on YouTube before. At that time, I purchased an IP starting with 38. Basically, their Hong Kong CMI also starts with 38, and when I pinged it with the webmaster tool, it showed China Hong Kong Cogent.
I found the contact information of this webmaster and inquired about the following:
Alright, that's the end of the story. I don't really understand these things, I just happened to not have tinkered around for a long time and my blog hasn't been updated for a while, so I just randomly messed around.